- Details
- Hits: 4107
Multiple Strategies Bring New Website Visitors

We agree with you, more new website traffic is necessary to be successful in running any online business. As it turns out, new visitor traffic is your lifeblood because it enables your business model to work and pay your bills every month. How to get it done is complex challenge for everyone. Our thought is with industry professionals evaluations like Credo's John Doherty setting the standards, you too can benefit from all professionals like us that do contribute to successful websites. Begin the process of implementing multiple strategies designed especially for you and your business. Make sure to bring new visitors, as well as new ways to include existing clients, and retarget those who may have been eager last year but now have budgets to work with. Multiple strategy implementation can be daily, weekly, monthly or even quarterly depending on your budget goals.
Not many companies on SEO and driving new traffic talk about existing clients and old site visitors for re-engaging their interests. If you are doing your job and your existing clients are happy; consider new products and service options geared toward your existing clients first. New budgets mean a fresh take on seeing results from last year. What worked, what didn't, and setting goals for 2017 and going forward. These existing clients are familiar with you, your current client relationships with them, and may be more able to consider these new strategies you have to offer.
Previous contacts by site visitors in 2016 are only an offering, call, or marketing piece away from one more opportunity at selling them new incentives for revenue. iComEx will help you formulate a way to contact these potential clients in a way which may surprise you just by a simple call to us. iComEx is a professional Web Site Development and Search Engine Optimization company in the Dallas / Fort Worth metropolitan area of North Texas, ready to assist you in achieving your organic search engine goals of which new site traffic is the end goal.
Consider iComEx SEO services including:
Here are some of our basic recommendations on driving traffic to your new or existing website in 2017: We would welcome an opportunity to help you with any or all of these new strategies on your own website.
- Create New Content On A Regular Basis - This ends the question of should i do seo; it's imperative really to be visible. By increasing the number of pages that can be indexed from organic traffic is with your targeted keywords, robots come out more and you stay relavent. High visibility equals site visitors who need your products and services.
- Be Sure To Continue To Optimize Older Content - Targeted keywords can be tracked in analytics and shown on specific pages. You find out what is working and what isn't and where you are on what page in Google. Google still leads in 85% of SEO so if you optimize for Google the other search engines will find you. Frequent new content means faster robot indexing and is always in your favor.
- Be Sure To Launch New Products & Services Often - Meet need with needs by your clients. In the sales conversion funnel, new services mean new income and keeping new opportunities for sales ever present. Frequent touch points with these new clients is important in the conversion process too. An opportunity for a newsletter or mailing just to them is welcomed when you are helping them increase your sales options and it's working.
- Create Online Courses For Education In Your Industry - Publish content targeted to your user needs and keywords and phrases. Research, analytics and keyword research to hand in hand helping to drive that traffic to your website and convert them into sales. You also add them to your ongoing marketing efforts at the same time and start creating your own list which can be divided into they type of list it is, and then send out appropriate marketing strategies to them throughout the year. Online course websites are out there in industries to post your courses to which can also help with generation of leads.
- Include Testimonials - Be sure to place Customer Service Testimonials in prime locations on your side bars for every page or at least the home page. Visible real success stories and customer satisfaction go a long way in driving traffic to your business or service based website and converting them to a sale.
- Consider Launching Infographics On Your Home Page - These useful graphics like on our iComEx home page tell a simple story, and help people to see and understand your content in a new way. Outreach of this type can be linked to all your existing Social Media as well and expose your company to a wider audience. Of course be sure to link back and forth to both the Media and your website for maximum exposure.
- Create a Google Account for all your Media and Videos - Posting these in appropriate pages where applicable in your website means you have a spokes person out there a click away from teach your potential new client about you, your company, products and services they may need. It only takes a moment to create a moment. One click to you can initiate a call by them for more information.
- Create Quick Forms For New Visitors Asking For More Information - A quick form requesting information, a quote, a service offering geared toward their company, or even a quick call to you is so easy. We are all busy, and work to the max every day. A simple easy form that can be done in a matter of minutes is so easy to get you started.
- Do You PodCast? Post Your Interviews - Grow a podcast audience means inviting influential people to your podcast. It's simply an audio version of a guest post or testimonial. Target podcast producers and get onto their shows
- Expand Appropriate Social Media For Your Needs - Facebook, Twitter, Pintrest, and the like are affordable. If your budget supports it, Adwords are an option but maximize that exposure to new websites, special offerings, or even consider permanent Press Releases all of which can be rotated on a regular basis quite easily. These have demographic options as well as the ability to target selected keywords that hit your target potential clients.
- Pay Per Click Can Be A Great Tool - When used for conversion oriented keywords, new audiences are ready to convert right away. Keeping specific to those markets or consumers is an additional strategy to try with new products and services as well.
Thank you for taking the time to look in on our iComEx website. For 20 years we have served the industry of small and medium size business clients in putting their websites to work for them. New strategies must bring change annually to insure sales and iComEx is here to help meet your current challenges this year. iComEx offers a variety of website services to business clients here in the United States, and we hope you consider our company as your option for 2017 in driving more traffic to your new or current website.
Building an Online Presence: Plan, Design, Execution, Manage
iComEx provides fully managed, boutique style web site hosting services, where we take a very hands-on approach to your needs. Utilizing scalable VPS hardware infrastructure, dedicated servers and best-of-breed enterprise hosting management solutions, backed by a 24/7 team of highly-trained network engineers, iComEx works proactively to prevent service interruptions and keep your website infrastructure up to date so you can stay focused on your business.
Advantage You.
Call us today. 972-712-2100 for a professional who will help you evaluate your current needs, or simply complete the form by clicking here: http://www.icomex.com/contact We look forward to speaking with you and getting started on meeting your needs with our services.
- Details
- Hits: 4362
Technique Being Exploited
Take a few minutes to read this. Phishing schemes abound. This one alert can go a long way toward protecting yourself and your business and family computer users from attacks like this one. Wordfence is a great source for keeping up to the minute on keeping your data safe.
This entry was posted in General Security, Miscellaneous on January 12, 2017 by Mark Maunder
Update at 11:30pm on Tuesday January 17th: I have received an official statement from Google regarding this issue. You can find the full update at the end of this post.
As you know, at Wordfence we occasionally send out alerts about security issues outside of the WordPress universe that are urgent and have a wide impact on our customers and readers. Unfortunately this is one of those alerts. There is a highly effective phishing technique stealing login credentials that is having a wide impact, even on experienced technical users.
I have written this post to be as easy to read and understand as possible. I deliberately left out technical details and focused on what you need to know to protect yourself against this phishing attack and other attacks like it in the hope of getting the word out, particularly among less technical users. Please share this once you have read it to help create awareness and protect the community.
The Phishing Attack: What you need to know
A new highly effective phishing technique targeting Gmail and other services has been gaining popularity during the past year among attackers. Over the past few weeks there have been reports of experienced technical users being hit by this.
This attack is currently being used to target Gmail customers and is also targeting other services.
The way the attack works is that an attacker will send an email to your Gmail account. That email may come from someone you know who has had their account hacked using this technique. It may also include something that looks like an image of an attachment you recognize from the sender.
You click on the image, expecting Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted by Gmail to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this….
![]()
You go ahead and sign in on a fully functional sign-in page that looks like this:
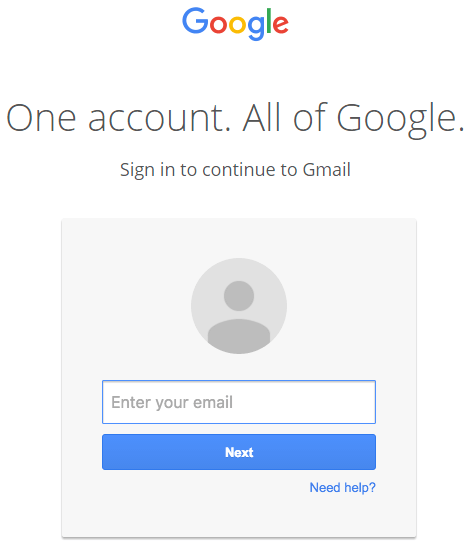
Once you complete sign-in, your account has been compromised. A commenter on Hacker News describes in clear terms what they experienced over the holiday break once they signed in to the fake page:
“The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.
For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
The attackers signing into your account happens very quickly. It may be automated or they may have a team standing by to process accounts as they are compromised.
Once they have access to your account, the attacker also has full access to all your emails including sent and received at this point and may download the whole lot.
Now that they control your email address, they could also compromise a wide variety of other services that you use by using the password reset mechanism including other email accounts, any SaaS services you use and much more.
What I have described above is a phishing attack that is used to steal usernames and passwords on Gmail. It is being used right now with a high success rate. However, this technique can be used to steal credentials from many other platforms with many variations in the basic technique.
How to protect yourself against this phishing attack
You have always been told: “Check the location bar in your browser to make sure you are on the correct website before signing in. That will avoid phishing attacks that steal your username and password.”
In the attack above, you did exactly that and saw ‘accounts.google.com‘ in the location bar, so you went ahead and signed in.
![]()
To protect yourself against this you need to change what you are checking in the location bar.
This phishing technique uses something called a ‘data URI’ to include a complete file in the browser location bar. When you glance up at the browser location bar and see ‘data:text/html…..’ that is actually a very long string of text. If you widen out the location bar it looks like this:
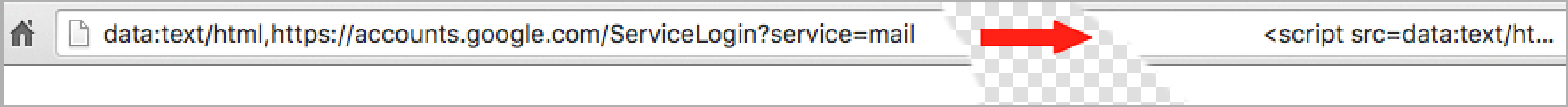
There is a lot of whitespace which I have removed. But on the far right you can see the beginning of what is a very large chunk of text. This is actually a file that opens in a new tab and creates a completely functional fake Gmail login page which sends your credentials to the attacker.
As you can see on the far left of the browser location bar, instead of ‘https’ you have ‘data:text/html,’ followed by the usual ‘https://accounts.google.com….’. If you aren’t paying close attention you will ignore the ‘data:text/html’ preamble and assume the URL is safe.
You are probably thinking you’re too smart to fall for this. It turns out that this attack has caught, or almost caught several technical users who have either tweeted, blogged or commented about it. There is a specific reason why this is so effective that has to do with human perception. I describe that in the next section.
How to protect yourself
When you sign in to any service, check the browser location bar and verify the protocol, then verify the hostname. It should look like this in Chrome when signing into Gmail or Google:
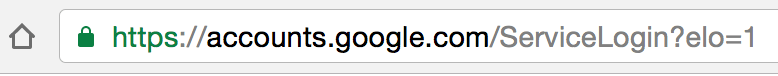
Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the lock symbol. You should also take special note of the green color and lock symbol that appears on the left. If you can’t verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page.
Enable two factor authentication if it is available on every service that you use. GMail calls this “2- step verification” and you can find out how to enable it on this page.
Enabling two factor authentication makes it much more difficult for an attacker to sign into a service that you use, even if they manage to steal your password using this technique. I would like to note that there is some discussion that indicates even two factor authentication may not protect against this attack. However I have not seen a proof of concept, so I can not confirm this.
Why Google won’t fix this and what they should do
Google’s response to a customer asking about this was as follows:
“The address bar remains one of the few trusted UI components of the browsers and is the only one that can be relied upon as to what origin are the users currently visiting. If the users pay no attention to the address bar, phishing and spoofing attack are – obviously – trivial. Unfortunately that’s how the web works, and any fix that would to try to e.g. detect phishing pages based on their look would be easily bypassable in hundreds of ways. The data: URL part here is not that important as you could have a phishing on any http[s] page just as well.”
This is likely a junior person within the organization based on the grammatical errors. I disagree with this response for a few reasons:
Google have modified the behavior of the address bar in the past to show a green protocol color when a page is using HTTPS and a lock icon to indicate it is secure.

They also use a different way of displaying the protocol when a page is insecure, marking it red with a line through it:
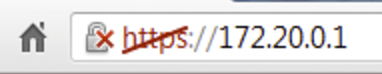
During this attack, a user sees neither green nor red. They see ordinary black text:
![]()
That is why this attack is so effective. In user interface design and in human perception, elements that are connected by uniform visual properties are perceived as being more related than elements that are not connected. [Read more: Gestalt principles of human perception and ‘uniform connectedness’ and Content Blindspots]
In this case the ‘data:text/html’ and the trusted hostname are the same color. That suggests to our perception that they’re related and the ‘data:text/html’ part either doesn’t matter or can be trusted.
What Google needs to do in this case is change the way ‘data:text/html’ is displayed in the browser. There may be scenarios where this is safe, so they could use an amber color with a unique icon. That would alert our perception to a difference and we would examine it more closely.
Update: How to check if your account is already compromised
I’ve had two requests in the comments about this so I’m adding this section now. (at 9:39am Pacific time, 12:39am EST).
There is no sure way to check if your account has been compromised. If in doubt, change your password immediately. Changing your password every few months is good practice in general.
If you use GMail, you can check your login activity to find out of someone else is signing into your account. Visit https://support.google.com/mail/answer/45938?hl=en for info. To use this feature, scroll to the bottom of your inbox and click “Details” (very small in the far lower right hand corner of the screen). This will show you all currently active sessions as well as your recent login history. If you see active logins from unknown sources, you can force close them. If you see any logins in your history from places you don’t know, you may have been hacked. [Thanks Ken, I pasted your comment in here almost verbatim. Very helpful.]
There is a trustworthy site run by Troy Hunt who is a well known security researcher where you can check if any of your email accounts have been part of a data leak. Troy’s site is https://haveibeenpwned.com/ and it is well known in security circles. Simply enter your email address and hit the button.
Troy aggregates data leaks into a database and gives you a way to look up your own email in that database to see if you have been part of a data breach. He also does a good job of actually verifying the data breaches he is sent.
Spread the word
I’ll be sharing this on Facebook to create awareness among my own family and friends. This attack is incredibly effective at fooling even technical users for the reasons I have explained above. I have the sense that most ordinary users will be easy pickings. Please share this with the community to help create awareness and prevent this from having a wider impact.
Mark Maunder – Wordfence Founder/CEO – @mmaunder
Update: Official Statement from Google
This is an update at 11:30pm PST on Tuesday the 17th of January 2017. I was contacted by Aaron Stein from Google Communications. He has provided the following official statement from Google:
“We’re aware of this issue and continue to strengthen our defenses against it. We help protect users from phishing attacks in a variety of ways, including: machine learning based detection of phishing messages, Safe Browsing warnings that notify users of dangerous links in emails and browsers, preventing suspicious account sign-ins, and more. Users can also activate two-step verification for additional account protection.”
I asked Aaron two follow-up questions:
“Chrome 56 will include the text “Not secure” in the location bar on non-SSL websites where a page contains a password field or credit card input field. This is a fine example of a visual indication in the location bar that helps secure users. Are the Chrome dev team considering some visual indication in the browser location bar for data URI’s? That would help defeat this attack because, currently, there is no visual indication of anything awry when viewing a phishing data URI. It’s worth noting that the safe browsing system is currently unable to detect malicious data URI’s because it is currently geared for traditional hostname-path URL’s.
Second question: Emails that contain malicious data URI’s are the attack vector in this case. Are the GMail team considering any additional filtering or alerting related to data URI’s as attachments in the GMail web application?
I think any guidance you can provide on the above two questions will go a long way to put Chrome and GMail user’s minds at ease.”
He responded with:
“I can’t speak to things that aren’t out yet, but *please* watch this space. Should have more to share soon”
My thoughts on this response:
I think this is a perfectly acceptable response from Google. To be clear, there are several teams within the Google organization that this affects:
The Google Chrome browser team will be the ones who would implement any change in the location bar behavior when viewing a phishing data URI. The GMail team would implement filtering and alerting within the GMail application with a data URI attachment is received with other associated phishing markers. The Google Safe Browsing team may add support for malicious data URI’s in the GSB API and make that available to the Chrome browser team.
There may be other parts of the Google organization that touches including operations.
Asking Aaron to provide early guidance on how Google will mitigate this when it affects so many teams was a big ask, but I would be remiss if I didn’t hit him with a couple of follow-up questions. The good news is that Google is aware of the issue and we have an official statement that indicates there will be something forthcoming in future releases of Chrome, GMail and possibly other products that can help mitigate this.
- Details
- Hits: 4088
1 Billion Accounts Have Data Stolen
Yahoo has announced another huge security breach, leaving its users fretting once again about their personal information.
We understand that if you have seen the latest news articles on mainstream TV, a serious breach of data by Yahoo is again making the news. Reports on all major news agencies say the latestest data thefts have affected more than one billion accounts, Yahoo (YHOO, Tech30) says. That's roughly double the number involved in the cybersecurity incident it announced in September, which is believed to be separate.
"Yahoo has now won the gold medal and the silver medal for the worst hacks in history," said Hemu Nigam, CEO of online security consultancy SSP Blue.
The embattled tech company said it's notifying users who may have been affected by the breach and making them change their passwords. The problem is it happened all the way back in August 2013. That means whoever plundered the information has had more than three years to exploit it, security experts say. But there are still several ways to make your information more secure.
Use different passwords for all online accounts
People who create a really strong password for one site but then use it across others are vulnerable to attacks, said Shuman Ghosemajumder, chief technology officer of Shape Security. Having your credentials stolen "is a matter of the lowest common denominator, the site with the least security," he said. Hackers obtained more than just names and passwords in the Yahoo breach -- they also nabbed answers to security questions. Cybercriminals can use that info to conduct automated attacks called "credential stuffing." That's when hackers take the stolen information of millions of users and build a program that tries to log in to other online accounts like banking, retail and airline rewards.
Yahoo is advising people to change the passwords and security answers on any other accounts for which they used the same or similar information as their Yahoo account. Since strong, unique passwords are a huge pain to memorize, Ghosemajumder recommends using a password manager. Platforms like 1Password or LastPass generate and store passwords and security answers for every account you have, so you only have to remember a single master password.
Beware of emails asking for more information
Hackers can use stolen credentials to craft emails that have the veneer of legitimacy, according to Nigam. Such emails might disclose the answer you gave to a security question, for example, and then ask if it's still up to date and request more information. "Criminals will give you information to gain your trust, and victimize you further," he said.
Related: Yahoo facing lawsuits in the wake of massive data breach
Be extra cautious about clicking on links or opening downloads from unknown email addresses. Never share any account information or passwords over email. Block access to your credit report Nigam recommends that you put "a freeze on your credit report and use a company that monitors your credit for you." Hackers who have valuable credentials will often try to open a credit card in your name.
Related: You could have a yahoo account without even knowing it
When that happens, the first thing a bank will do is run a credit check. If you've put a freeze on your credit report, you will be alerted that an institution is trying to run a check and can flag that you didn't request it.
"I would strongly recommend it, even if you don't have a Yahoo account," Nigam said. It's not all on you. Companies need to step up security measures to protect themselves not only against hacking, but also against the aftereffects of hacking like credential stuffing attacks, according to Ghosemajumder. "The trust that your users have in you is directly tied to the level of security they expect," he said. But what about closing accounts? After two major breaches, is it time to say goodbye to Yahoo?
Related: What to do if your Yahoo account was hacked
"If you don't have confidence [in Yahoo] in the future, that's a personal decision people need to make," Ghosemajumder said, noting that Yahoo has a large security team and has invested heavily in security.
"But I think this is a severe setback for them and the entire company," he added.
-- Heather Kelly contributed to this report. http://money.cnn.com/2016/12/15/technology/yahoo-security-breach-billion-users/
Yahoo released its semiannual transparency report today, the first issued by the company since Reuters revealed earlier this month that Yahoo scanned its users’ email accounts at the behest of the U.S. government.
In an effort to inform consumers about how frequently the government snoops on their information, and how often companies are able to narrow or refuse the requests, Yahoo and many other technology companies make public on a regular basis data about requests from law enforcement agencies for user data.
“We review demands for narrowness, legal sufficiency, duration, and scope, and consider all appropriate options before we comply, including seeking clarification or modification of the demand, or even challenging the demand in court,” Yahoo general counsel Ron Bell wrote in a blog post accompanying the transparency report.
Bell was reportedly one of the Yahoo executives, along with CEO Marissa Mayer, who approved the installation of software in spring 2015 that scanned Yahoo email accounts for specific data. The software was quickly discovered by members of Yahoo’s security team, who initially believed hackers had broken in and installed the program. The resulting clash between leadership and security engineers reportedly lead to the departure of chief information security officer Alex Stamos.
As we previously reported, Yaho’s spring 2015 transparency report does not reflect an unusually high number data disclosures to the government, as might be expected from a dragnet email scanning program. At the time, the company only reported 21,000-21,499 user accounts requested under the Foreign Intelligence Surveillance Act and 0-499 accounts requested with National Security Letters. However, Yahoo allegedly scanned all of its nearly 300 million users’ email accounts — a vastly larger group than reported.
- Details
- Hits: 4192

Stay Safe Online For All Your Gifting!
It's important to take steps to protect yourself when shopping online during this Holiday Season. We realize there are so many more options to purchase online this year, and statistics for Black Friday and Cyber Monday indicated that almost 40% more shoppers purchased online that they did last year. Great news for shopping but you need to make sure you do all you can to eliminate compromise of your data. Please take a few minutes to read this article below. Stay safe online is a great resource for finding out the best accepted standards procedures you can implement in your technology from the home computer to your phone purchases.
Anything connected to the Internet, including mobile devices like smartphones and tablets need to be protected – especially during heavy use periods, like the holidays. Scammers and cybercriminals can target shoppers as well. Everyone should be on alert for emails that might get us to act quickly and click through links and open attachments. Be wary of emails about problems with your credit cards or an account or the status of online order. The bad guys know we are price sensitive when shopping online. Exercise caution when seeing and ad offer where the discount is way below normal. Being a safe and secure shopper starts with STOP. THINK. CONNECT.: Take security precautions, think about the consequences of your actions online and enjoy the conveniences of technology with peace of mind while you shop online. Remember these tips during all online purchases.
Online Shopping Tips:
- Conduct research: When using a new website for purchases, read reviews and see if other consumers have had a positive or negative experience with the site.
- When in doubt, throw it out: Links in emails, posts and texts are often the ways cybercriminals try to steal your information or infect your devices.
- Personal information is like money: value it and protect it: When making a purchase online, be alert to the kinds of information being collected to complete the transaction. Make sure you think it is necessary for the vendor to request that information. Remember, you only need to fill out required fields at checkout.
- Use safe payment options: Credit cards are generally the safest option because they allow buyers to seek a credit from the issuer if the product isn’t delivered or isn’t what was ordered.
- Don’t be disappointed: Read return and other polices so you know what to expect if the purchase doesn’t go as planned.
- Protect your $$: When shopping, check to be sure the site is security enabled. Look for web addresses with https:// indicating extra measures to help secure your information.
Shopping On the Go:
Now you see me, now you don’t: Some stores and other locations look for devices with Wi-Fi or Bluetooth turned on to track your movements while you are within range. Disable Wi-Fi and Bluetooth when not in use.
Get savvy about Wi-Fi hotspots: Limit the type of business you conduct over open public Wi-Fi connections, including logging on to key accounts, such as email and banking. Adjust the security settings on your device to limit who can access your phone.
Basic Safety and Security Tips:
- Keep a clean machine: Keep all web-connected devices ‒ including PCs, smartphones and tablets ‒ free from malware and infections by running only the most current versions of software and apps.
Lock down your login: Fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking and social media. - Make your password a sentence: A strong password is a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember (for example, “I love country music.”). On many sites, you can even use spaces!
- Unique account, unique password: Having separate passwords for every account helps to thwart cybercriminals. At a minimum, separate your work and personal accounts and make sure that your critical accountshave the strongest passwords.
Do not be afraid to ask for help with your best practices if you don't understand some of what this article above is explaining to you. Your skillset may not be in the tech based industry and our qualified staff here at iComEx can help you make sure all your computers are as safe as they can be. We have regular maintenance plans available to help make sure your Holiday Season Gifting goes smoothly. Call us today at 972-712-2100.
http://staysafeonline.org/ Thank you Stay Safe for all the information you have on your website.
- Details
- Hits: 3641
Protect Yourself This Holiday!

Each person must understand that passwords are like keys to your personal home online. Bearing that in mind; iComEx encourages you to do everything you can prevent people from gaining access to your passwords. You can also further secure all your accounts by using additional authentication methods. Here is a great article reprinted from stay safe online that may help you in the upcoming Holiday Season.
Passwords - Passwords can be inconvenient, but they’re important if you want to keep your information safe.
- Protecting your personal information starts with STOP. THINK. CONNECT.: take security precautions, think about the consequences of your actions online and enjoy the Internet with peace of mind. Here are some simple ways to secure your accounts through better password practices.
- Make your password a sentence: A strong password is a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember (for example, “I love country music.”). On many sites, you can even use spaces!
- Unique account, unique password: Having separate passwords for every account helps to thwart cybercriminals. At a minimum, separate your work and personal accounts and make sure that your critical accounts have the strongest passwords.
- Write it down and keep it safe: Everyone can forget a password. Keep a list that’s stored in a safe, secure place away from your computer. You can alternatively use a service like a password manager to keep track of your passwords.
Other Ways to Secure an Account - Typing a username and password into a website isn't the only way to identify yourself on the web services you use.
- Lock down your login: Fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking and social media.
Over time, more websites will be adopting multi-factor authentication. In some cases, the services may be available but are not required.
Many email services offer two-step verification on an opt-in basis. Ask your financial institution, email provider and other online services if they offer multi-factor authentication or additional ways to verify your identity.
Articles by: Staysafeonline.org For more information about online safety and obtaining training, information graphics and most issues facing us today please take a look and get involved today.



